Secure Flash for Next-Generation Automotive and Industrial Applications
December 20, 2019
Story

Connected devices are vulnerable to cyberattack, so it follows that advancements in autonomous driving and industrial automation come with greater risk.
Connected devices are vulnerable to cyberattack, so it follows that advancements in autonomous driving and industrial automation come with greater risk. Communicating to the cloud, processing software updates, and capturing diagnostic data comprise an ever-growing attack surface. The devices themselves can also be tampered with, but physical attacks such as these generally do not scale.
It's increasingly important that connected devices take a holistic approach to security, beginning with a secure boot process. Boot code must be authenticated and stored securely in non-volatile memory (NVM). This article will explore how technological advancements are driving system architecture changes for processor and memory, but let’s first understand the evolution of security in embedded systems.
Evolution of Security in Embedded Systems
For many years, smart cards and hardware security modules (HSM) have provided a discrete “secure enclave” where cryptography can be performed. These peripherals include a significant amount of reprogrammable NVM (EEPROM or Flash) that allows secrets to be stored within the secure enclave, protected from malicious attacks or accidental compromise. These devices are slave peripherals to a host controller and are used in a wide variety of applications.
In 2006, a group of German auto manufacturers developed the Secure Hardware Extension (SHE) specification, defining a minimalist HSM that could be integrated into a chipset. The SHE architecture has been widely adopted by secure chipsets designed for the automotive market. SHE was implemented as a state machine with cryptographic functions based on the Advanced Encryption Standard (AES) algorithm and included enough NVM to store the required keys and counters.
Within a few years, the automotive industry recognized that higher levels of security were required in certain automotive applications. From this, the EVITA Workgroup was created. SHE was adopted as a basis for the EVITA Light HSM, but more advanced versions were defined for medium and high security applications. The EVITA Medium and EVITA Full HSMs built upon the legacy SHE infrastructure and added an ARM CPU to manage HSM operations. Finally, Elliptic Curve Cryptography (ECC) was added to the EVITA Full HSM to achieve an even higher level of security. The EVITA Workgroup’s HSM variants are widely deployed and are the basis for much of the security infrastructure described in the currently active AutoSAR Working Group.
Disappearance of Embedded Flash on Advanced Process Nodes
Secure enclaves generally rely on embedded Flash (eFlash) for storage of keys and other cryptographic information. Embedded Flash is commonly available on foundry process nodes of 40nm and larger, and a few examples even exist at 28nm. However, as process nodes continue to shrink, the integration of eFlash is becoming exceedingly difficult due to both device physics and economics. Foundries are spending considerable effort searching for small-geometry, embedded NVM but so far, no viable solutions have emerged. Small-geometry RRAM and MRAM have been extensively explored as eFlash alternatives but are not yet viable, especially for mission critical applications requiring high reliability at high temperatures. It is not clear when (or if) any of these technologies will be placed into production. As a result, developers are using external Flash in place of eFlash.
Today’s systems use a standard QSPI NOR Flash memory with the acknowledged shortcoming that the external NOR device is not secure (see Figure 1). A leap forward is to use a Secure Flash device to dramatically improve security and to satisfy the HSM’s requirement for a secure reprogrammable NVM. The critical function is to create a secure channel where bits can be exchanged between the HSM and a cryptographically secure region within the Secure Flash device.

Figure 1: The evolution from embedded to external secure Flash.
Cryptographically Secure Storage: Secure Flash can enable hardware-protected secure storage for security keys, certificates, password hashes, application-specific data and configuration data, code version information, and biometric sensor data for authentication. In addition, it can support authenticated and encrypted transactions to protect against unauthorized access and other security threats.
Fast Secure Boot: Automotive applications rely on fast secure boot. A typical CAN bus in automotive applications has a startup requirement of less than 100ms. That means an ECU must be able to reply to CAN messages within 100ms after power on. If a CAN node is not able to boot within 100ms, it might miss critical CAN messages, which is unacceptable for automotive applications such as ADAS. A secure Flash device can enable a secure boot process to mutually authenticate with the Host MCU and ensure bus transaction confidentiality and authenticity in less than 100ms.
Secure Firmware-Over-The-Air (FOTA) Updates: The average automobile contains approximately 100 Electronic Control Units (ECU) and over 100 million lines of software code. We trust these systems to handle more tasks with greater complexity, which punctuates the need for increased reliability and end-to-end security. Since code and data reside on an external Flash, protecting the Flash from attack is critical to ensure data integrity, authenticity, and immunity to replay attacks. A secure Flash provides end-to-end protection by allowing only authorized updates and enabling a hardware root-of-trust to prevent modifications, manipulation, and other security attacks on code and data storage. Secure Flash also makes systems in the connected world more secure by offering encrypted and authenticated transactions between the host MCU, secure storage, and cloud (see Figure 2).

Figure 2: Secure FOTA Update with Secure NOR Flash
Automotive Applications
The automotive market is a leading adopter of secure Flash. Primary applications include advanced driver assistance systems (ADAS), gateways, telematics, instrument clusters, and engine/powertrain controls. Use cases span code/data storage, fast secure boot and firmware-over-the-air (FOTA) updates. ADAS, gateway and HEV/EV powertrain applications continue to be the growth drivers in this market segment.
Advanced Driver Assistance Systems (ADAS): ADAS detects objects, alerts the driver of hazardous conditions or impending danger, keeps a car in a lane, and slows down or stops the vehicle automatically. ADAS applications include night vision assist, driver monitoring, pedestrian and traffic sign recognition, forward collision warning, lane departure warning, and blind spot monitoring (see Figure 3). In an ADAS system, the safety-critical algorithms and data are stored in the Flash memory. Therefore, it is critical to ensure that the Flash contents are not tampered with in any way. In addition, OEMs expect to perform OTA firmware updates, further complicating security challenges. A secure Flash is well-suited for ADAS applications, as they ensure secure, safe, reliable program execution and secure storage of critical data, even in extreme temperatures. For example, Cypress NOR Flash devices are available with AEC-Q100 automotive-grade qualification and are ISO 26262 ASIL-B compliant.
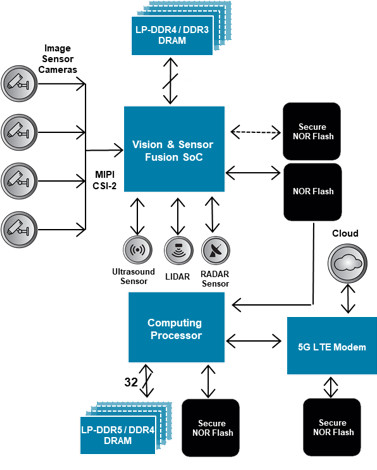
Figure 3: Block Diagram of a Typical ADAS System
Connected Car: Communications between vehicles and remote entities is becoming increasingly common for operations including software updates, remote capturing of diagnostic data, and communications with transportation infrastructure (LTE, Wi-Fi channels). In-vehicle communications between Electronic Control Units (ECUs) through CAN and Ethernet busses are essential to ensure proper functionality (see Figure 4). In each of these communications subsystems, one of the most critical electronic components is the memory used in the ECU. An attack on an ECU memory can result in data leakage, unreliable behavior, or even catastrophic failure. If the electronics in a modern automobile is to be secure, the memory subsystem must be made to resist attacks from malicious actors.
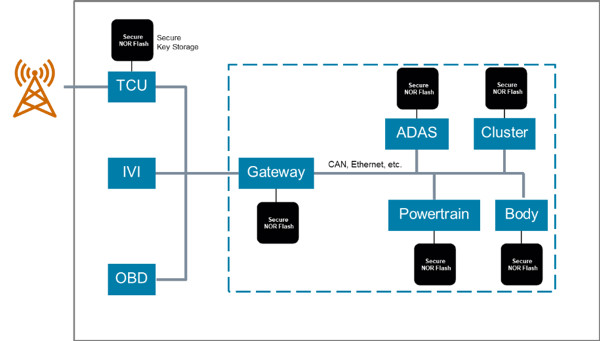
Figure 4: Typical In-Vehicle Network
Industrial Applications
Industry 4.0 smart factories utilize cyber-physical systems to monitor physical processes and create a virtual copy of the physical world for new and decentralized decision-making capabilities. Industrial IoT (IIoT) devices connect to local systems and the cloud, and leverage machine learning to increase productivity, quality and safety. These systems monitor, manage and control the factory, manufacturing only what is needed, when it is needed, and with proper authorization. Many of these IIoT systems require high levels of security, high reliability and low power in all operating modes. Secure Flash is a good fit for industrial automation, industrial cameras, medical equipment, measurement equipment, industrial computing, M2M communication, and more.
Industrial Machine Vision Camera: Tiny high-resolution wired and wireless cameras combine with image processors to enable machines to see, interpret, plan, and act. This technology is transforming security, manufacturing, healthcare and retail industries. Today’s industrial machine vision cameras are sophisticated systems that combine image processing, real-time pattern matching, and object tracking, all while communicating over network interfaces and controlling multiple motors under extreme operating conditions (see Figure 5). Secure Flash is suited to meet these requirements by supporting fast secure execution, code protection, and industrial temperature ranges.

Figure 5: Typical Machine Vision Camera
Secure external Flash is gaining momentum as an alternative to eFlash, which has become scarce as process nodes shrink below 40nm. We need HSM integrated into a Flash technology for secure chipsets that are not able to integrate eFlash. Chipsets that can integrate eFlash but need additional non-volatile memory dedicated to HSM functionality will also find secure Flash attractive. Secure Flash allows data to be transported between a protected area within its user array to the Host MCU’s HSM over existing communication infrastructure in a cryptographically secure manner.
An advanced secure Flash can be created by leveraging the in-memory computing capabilities of modern NOR Flash devices such as Cypress’ Semper NOR Flash which integrates an ARM Cortex M0 processor. Advanced security includes features to protect against overwriting, modification, and manipulation attacks on firmware, boot images and system parameters. Secure Flash becomes a fundamental part of enabling functionality safety as well.
Using existing bus protocols including QSPI and xSPI, a Secure Flash device can work with Host MCUs to achieve the security levels required in demanding connected applications while retaining compatibility with existing host memory controllers. Current state-machine based memory architectures do not offer the same flexibility and programmability as an embedded core. An embedded ARM Cortex M0 enables a superior architecture that adds hardware crypto acceleration, secure HMAC key generation and storage, and uses monotonic counters to address broad security concerns of automotive and industrial embedded systems (see Figure 6).

Figure 6: Secure Flash Architecture (Cypress Semper NOR Flash)
For more information about Cypress Secure Flash, visit [email protected].




