The Cavalry has arrived for automotive cybersecurity. What's next?
July 29, 2015

After the publication of Charlie Miller and Chris Valasek's remote commandeering of a Jeep's CAN bus brought national attention to the issue of automo...
After the publication of Charlie Miller and Chris Valasek’s remote commandeering of a Jeep’s CAN bus brought national attention to the issue of automotive cybersecurity, many consumers have been left asking, “How do we know our vehicles are safe?” A year after releasing the Five Star Automotive Cyber Safety Framework, members of I Am The Cavalry, a grassroots white hat security organization, are working with automakers, legislators, and regulators to answer that question.
There was a recent comment on a guest blog by Airbiquity’s Scott Frank entitled “Is the hysteria around connected car hacking built on truth?” that stated:
“The safety of consumer products depends on the willingness of consumers and activists to fight for (and be willing to pay for) that safety. It certainly doesn’t happen by accident, and often just doesn’t happen.”
Thinking about big business, this really resonates. In the case of the connected car (and vehicles in general), what gives automakers the incentive to break away from the status quo? Outside of bad press, there is often no force capable of driving change within insular industries other than a consumer’s wallet, and the inherent fault with the latter is that consumers may not be educated enough on topics such as vehicle cybersecurity to know what they don’t know. And, without pointing fingers, how would they?
About a year ago, a grassroots organization called I Am The Cavalry (www.iamthecavalry.org) attempted to bridge the gap between consumer awareness and automotive cybersecurity with the publication of the Five Star Automotive Cyber Safety Framework at the annual DEF CON Security Conference in Las Vegas. Several media outlets picked up the story, illuminating the organization’s thoughts on the need for collaboration between auto manufacturers and the tech sector to mitigate threats to vehicle subsystems that control adaptive cruise control, electronic braking, parking assist, and remote assistance, among others. The Framework proposed that such a collaboration address security in five steps:
- Safety by design achieved through the use of standards, a reduction of in-vehicle attack surfaces, more rigorous demands on supply chain transparency, and the implementation of individual and adversarial resilience testing practices
- Third-party collaboration based on legitimate industry standards from the ISO, for example, as well as full cross-industry disclosure of known vulnerabilities and positive incentives that stimulate participation in such efforts
- Evidence capture that relies on lowest common denominator standards for logging and legal syntax to avoid confusion and improve National Highway Transportation Safety Administration (NHTSA) investigations through increased causal analysis capabilities, all while remaining sensitive to data privacy concerns
- Security updates built around verified secure update systems, service-level agreements (SLAs) that promote fast delivery of fixes, and transparent public notification and communications frameworks
- Segmentation and isolation that create air gaps between critical and non-critical vehicle systems, ensure system integrity and/or recovery, and provide enhanced assurance via third-party reviews
The move was received well by the public, with more than 650 individuals supporting “An Open Letter to the Automotive Industry: Collaborating for Safety” through an online petition, 405 active threads on a Google discussion forum, and daily interactions with more than 3,000 followers on Twitter. But almost a year after calling The Cavalry and realizing that it is us, where are we now?
We are The Cavalry
Before looking to the future, for context it’s necessary to investigate the beginnings of I Am the Cavalry, which was officially established in 2013 with the goal of raising awareness around the precarious nature of connected technology in the medical, Internet of Things (IoT), public infrastructure, and automotive sectors. Over time, hackers and researchers from the white hat development community, along with technical and non-technical individuals from affected industries, began contributing to the group, and eventually The Cavalry grew into the equivalent of an educational foundation (I Am The Cavalry is currently applying for 501(c)(3) status) that both facilitates public discourse and promotes a collaborative approach to cybersecurity for technology-dependent, safety-critical systems.
Looking to make an immediate impact, The Cavalry focused initial efforts on the automotive industry, where increasing amounts of code and connectivity are broadening the attack surface in modern production vehicles, as evident in a recently published article in WIRED magazine that describes Charlie Miller and Chris Valasek commandeering a Jeep’s CAN bus to assume control of the vehicle. As a result, I Am The Cavalry embarked on a mission to create a multi-stakeholder cybersecurity posture against adversaries and accidents that both preserves public safety and protects the interests of an industry that accounts for a double-digit percentage of the U.S. economy, says Josh Corman, Co-Founder, I Am The Cavalry.
“What’s happening now that we’re putting software into things that can kill you is there’s this massive [cybersecurity] gap in the middle that is not privacy, and it’s not traditional safety – it’s cyber safety,” Corman says. “It’s becoming super clear to me that a central problem in this whole thing is that when you talk to talk to physical or traditional engineers for cars, the word ‘safety’ means something very specific to them, and it usually means validating intended use. So there are a bunch of things a car is supposed to do, and they validate it a lot. Then there’s security that means something very specific as well to the people that tend to be working on the IT systems within the car. The problem is when you say ‘security,’ they’re thinking of just the security of the IT, and when you say ‘safety’ they’re thinking of just the intended use of the vehicle and physical systems.
“All hacking lies outside of intended use – all hacking,” he continues. “You’re making systems do things they weren’t designed to do, and if there aren’t protected measures in your threat modeling and if you’re not containing and isolating, segmenting logically, then even though this radio should never send commands to bleed the brake lines the fact that it can if it was subverted with an evil Facebook app through the app store means it could send the same CAN message. Short of any segmentation, isolation, abuse, and unintended use filter, [hackers] could and can and have issued malfeasant commands. It’s not okay to say, ‘the car is safe, that’s the Progressive Snapshot dongle’ because the car’s architecture allowed the ODBII port dongle to send commands on an open, flat CAN bus, which can therefore be a stepping stone to send fake messages to bleed brake lines.
“What we keep telling [automakers] is, ‘It’s not an if one of you is going to get hacked publicly, it’s a when. And when that moment comes, it doesn’t matter which one of you gets hit, it’s going to hurt all of you. So you better have your ducks in a row before you need to,’” says Corman. “The Five Star is basically saying all systems fail. In fact, we should have made star zero be “all systems fail” because the rest of it makes sense afterwards, as ‘therefore, this is why you need these five ready postures towards failure.’ If you look past the formal names, the first one is saying, ‘tell us how you avoid failure.’ The second one says, ‘tell us how you’ll take help avoiding failure.’ Third is, ‘how do you notice and learn from failure.’ Fourth is, ‘how do you respond quickly to failure.’ And fifth is how do you contain and isolate failure. And who can deny that these systems will fail, even if it’s just accidents? It’s accidents and adversaries, and as such [the Five Star] is a really elegant, minimum table stakes approach to failure.
“We see a lot of car companies doing a lot of the right kinds of things, not everywhere across all five, but a lot of them are doing good things. It’s just none of them will talk about what they’re doing. This is a fairly problematic cultural defect, and I understand why they feel this way, it’s just the wrong posture,” he explains. “That closed attitude and culture fails to instill confidence in the American public. Microsoft, for years, was doing court injunctions and third-party relationships with adversarial researchers, and fast forward 20 years later, it’s a vital and necessary, vibrant part of their culture, and they couldn’t live without it. We want to compress the mean time to enlightenment from 20 years – like it had to be in the IT world – to three years. They’re going to get enlightened, but can we compress that mean time to enlightenment, especially with public safety on the line here?”
I Am The Cavalry – One year later
Despite a deep-seated culture of mistrust in the auto industry brought on by decades of competition, I Am The Cavalry has started to make inroads with automakers and Tier 1s a year after releasing the Five Star Automotive Cyber Safety Framework. Though the early days were fraught with skepticism and most industry players still tread carefully around technical concepts like the universal automotive black box (Sidebar 1), recent developments such as the Security and Privacy in Your Car (SPY Car) Act based loosely on the Five Star and NHTSA fines levied against Fiat Chrysler may be contributing factors in moving automakers to action on the cybersecurity front (for more on the SPY Car Act, read a recent blog by Gene Carter of Security Innovation).
“For the first couple of months after we launched the Five Star people didn’t know who we were, what our motives were. Were we going to try to extort them? Were we going to drop a bunch of zero day attacks on them like other people have? They were generally interested in the collaborative approach we were outlining, but they didn’t know us yet and were looking into us.” Corman recalls. “I think after that period people understood our angle and started the trust relationships, and it happened one OEM or one person at one OEM at a time, but we started getting to participate in workshops at the end of last year. Heading into this year we’ve been at about one automotive conference per month, at things like the SAE events in Detroit and BDI in Germany. So we’ve gone from, ‘who are they?’ to ‘let’s debate the Five Star,’ and the end of May was the tipping point because we seemed to stop debating it around the time of the Markey bill and the class-action Toyota lawsuit. I phrased this as, ‘Guys, you’re going to end up having to do something. The government prefers self-regulatory over heavy-handed government, so if you embrace this maybe you can stave off external regulation. The thing is that laws are hard to change and technology changes really, really fast. So, if you don’t take control and keep yourself in the driver’s seat, the laws will make it even harder to do the right thing.’
Sidebar 1 | Automotive black boxes and privacy versus safety
“The joke we’ve been making is that we love our privacy, but we’d like to be alive to enjoy it,” says Corman as he turns his attention to star three of the Five Star Automotive Cyber Safety Framework. Perhaps the most controversial element of the document, the “Evidence Capture” portion of the Five Star calls for either a “black box” architecture, or at least some standard lowest common denominator taxonomy that enables system monitoring and recording in vehicles. Similar to how syslogging and Linux logs operate on other computing platforms, a widespread or universal structure or specification that facilitates vehicle event recording would enable automakers, insurers, regulatory bodies, and others concerned with unprecedented insight into vehicle failures and malfunctions, as well as their possible causes. For example, Corman points to how such a system could be applied to help with adjudication in cases like the Toyota unintended acceleration lawsuit, rather than relying on skid marks.
However, the idea of adding a tamper-evident, black box-type of technology to personal property brings with it glaring questions around privacy rights. Short of a legal mandate, most car companies will be hesitant to join the rank and file of surveillance violators and data breached companies, making the prospects for the Five Star’s Evidence Capture portion “the one that scares me the most,” says Corman.
“One of the reasons that [a black box] is critically important is you cannot simultaneously decry and scream that there is no evidence of hacking when you have no ability to collect evidence of hacking. One way to fix this is to put in the scaffolding now,” Corman says. “If people were hacking and if some percentage of deaths in the U.S. automobile death count were due to hacking, wouldn’t we want to know about that? Wouldn’t we want to know about the frequency and the type of attacks that are being done such that we could extrapolate that to make sure that other car companies aren’t targeted next?
“If you talk to the industry, they believe as soon as you say ‘black box’ that that’s a legal quagmire,” he explains. “No, it’s not, actually. You don’t have to track their movements, you don’t have to track what they were doing on the radio while they were driving and should have been paying attention to the road, you simply have to track the integrity of the system and whether it did things that deviate from normal behavior. Was there an unauthorized action? Was there a flood of data?
“If it’s going to take five years to build it, let’s start that five year journey now,” he continues. “Short of doing it, we won’t be able to capture and learn from it, and furthermore, these things protect everybody because if in fact this black box can prove that the car was modified then the car company won’t be sued when a death happens. If it’s proved that this was malicious tampering then you can’t blame the driver for running a red light because someone hacked the brakes. It places the appropriate burden of proof on the evidence to protect all parties involved with truth instead of hearsay or other types of evidence.”
Furthermore, Corman uses to the business case for black boxes in other forms of transportation as a model for automotive, as the lessons learned in the airline industry, for example, have permitted the National Transportation Safety Board (NTSB) to work with airlines to safeguard future passengers and the market itself. In the case of auto, black box technology could be used to better inform NHTSA and the Federal Trade Commission (FTC) of notable failures or possible hacks (see SPY Car act), though the safety and economic benefits translate directly, Corman asserts.
“The business case has already been made,” says Corman. “The social good and the public safety that comes out of black boxes and the NTSB saves no one on the airplane that crashed, but what it does do is save future passengers on future aircraft,” Corman says. “And it’s also not about the one plane company, it’s about the industry. It’s also not just about the actual life, it’s about the economics, and this is something that the regulators really understand. One of the reasons the NTSB is necessary is that if the international flying public were to lose any confidence in the airline industry, think of the GDP impact on any material change of confidence in flying. There are reasons we do this, and the very same reasons we do this elsewhere apply to cars.
“I have no interest finding and fixing one flaw in one car from one manufacturer. I’m here to make sure the entire auto industry gets better,” he concludes.
“While we’ve made significant progress in this first year educating them on these five ready postures towards failure and starting to frame how they’re approaching fixing many of them, they’re furthest along on number one, which is they all have some sort of plan they’re executing on their software development life cycle (SDL), just none of them are announcing what it is,” says Corman. “Number two, the only one that has a third-party collaboration posted is Tesla, and they’ve gone to step two by adding a bug bounty. Number three, there are state laws that require some nominal amount of event recording, but they’re not recording system integrity and they’re not recording it consistently – so the big tamper-evident forensic black box that could help the NTSB is a ways off because they’re still debating if it’s entangled with civil liberties or not, they’re still debating if it’s going to happen or not, and they don’t even have design plans and even if they did it wouldn’t be done for a while.
“Secure updates have been indirectly revealed, and we already know that Tesla does them; Ford has announced they’re going to do them; BMW we know for a fact is doing them in some vehicles because the hack that they fixed they fixed over the air (Sidebar 2),” he explains. “Then, for segmentation and isolation, we know that the new Teslas, because they’ve been very open about it at DEF CON, have a multi-CAN bus, tiered architecture design that they’re implementing for future vehicles, but we haven’t seen much openness from the other guys about how they’re doing segmentation and isolation, just that they know that the big, wide, flat open network isn’t necessarily a good idea.”
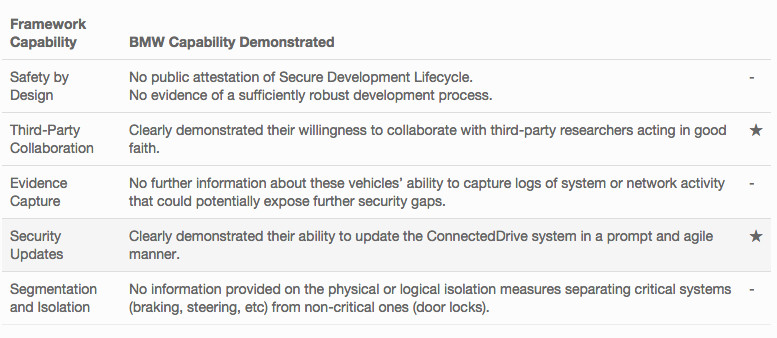
Sidebar 2 | BMW gets two stars for latest security update
BMW recently conducted an over-the-air (OTA) update to fix a flaw with the door lock system in more than 2 million of their vehicles that allowed persons other than the driver to unlock doors remotely. The remote updates came after the German Automobile Association (ADAC) identified six flaws in the automaker’s ConnectedDrive system, disclosed them to BMW, and worked collaboratively with the company to patch the vulnerability using server authentication checks and HTTPS encryption.
In addition to collaborating with a third party on vehicle cybersecurity (Star 2), BMW also demonstrated their ability to administer security patches in a prompt and agile manner (Star 4), checking off two boxes in I Am The Cavalry’s Five Star Automotive Cyber Safety Framework (Figure 1). Though there is still room for improvement in the eyes of Cavalry members and others, the execution of these updates illustrates the benefits of relationships with adversarial researchers for consumers and carmakers alike.
For a more in-depth recap of the update from a Cavalry perspective, read their blog.
 |
We are The Cavalry for automotive cybersecurity. What’s next?
Today, I Am The Cavalry continues to roll the momentum it has gained over the past year into relationships and strategies it believes will lay a foundation of trust and safety in future vehicles, for consumers and the auto industry alike. While the organization cautions carmakers against repeating past mistakes with open, unsegmented system architectures and ad hoc security measures, Corman stresses that I Am The Cavalry’s focus remains on being a trusted cybersecurity partner for automakers that advocates for the social good, rather than judge and jury in the court of public opinion.
“One of the things that’s preventing [automakers] from making future progress is that they’re so focused on the current fleet and focused on using aftermarket solutions like intrusion defense systems (IDSs) from Israel or ARGUS or this or that, that the danger they face is that they’re going to make the same mistake the private sector made with bolt-on security,” he explains. “Bolt-on is always more expensive, always adds an attack surface, and always has less efficacy. Built-in is the way to go, but when they look at the old fleet it prevents them from thinking clearly about the new fleet. What I’ve tried to encourage at every single one of these watering holes and every engagement we’ve ever had with any of them is that you need one plan for the current exposure and you need a different plan, a better plan for the future exposure, or we’re never going to get these things in balance. The good news is that the older the vehicle is the less hackable it is remotely, but the bad news is while they’re focused on the older fleet they are continuing to make new bad decisions for the newer fleet.
“We want to be a helping hand, not a pointing finger. We want to work with you in private, not pound you in public. We want to be focused not on past failures, but on future successes. We don’t want to be focused on offensive techniques, we want to be focused on defensive architectures,” Corman continues. “We believe that if we can get one of them to declare to the Five Star that the others will have to, so we’re trying a bunch of stuff. We’re doing the right thing and we’re being honest brokers and we’re using facts and logic and empathy, and we’ll see where it goes. Sometimes it’s just about being that helping hand and teammate and ambassador until they’re ready. There’s going to be some moment when they’re going to be ready – that Cuyahoga River on fire moment when people realize that maybe we’re polluting too much, the river is on fire.”
If you’re interested in more thoughts on security deficiencies in the tech industry, watch Corman’s TED talk below.





